Hello, I am not very expert in R and Shiny. I hope you can help me
what happens is that I had to do a simple project for shinyapps.io, but for the project to be approved by my company, it must pass a vulnerability scan and a pentest.
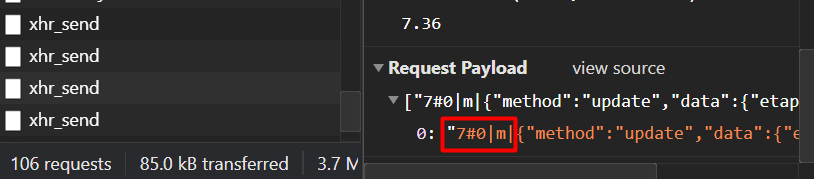
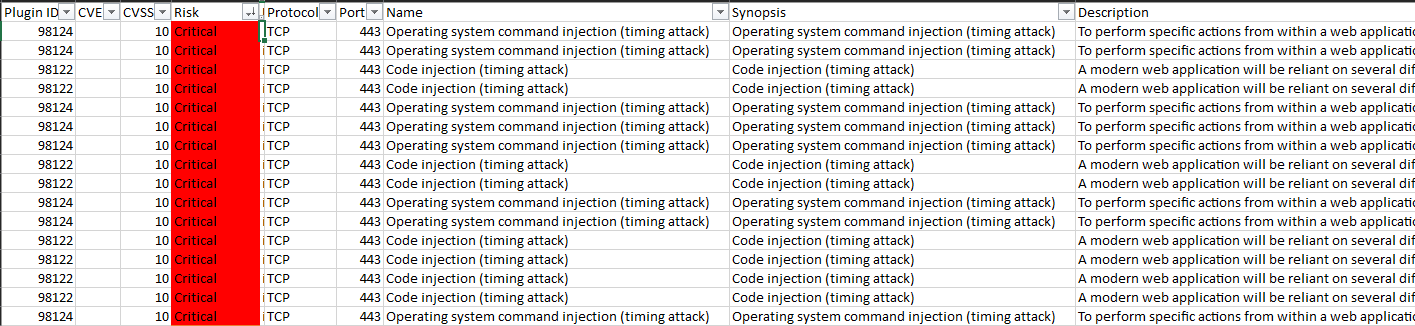
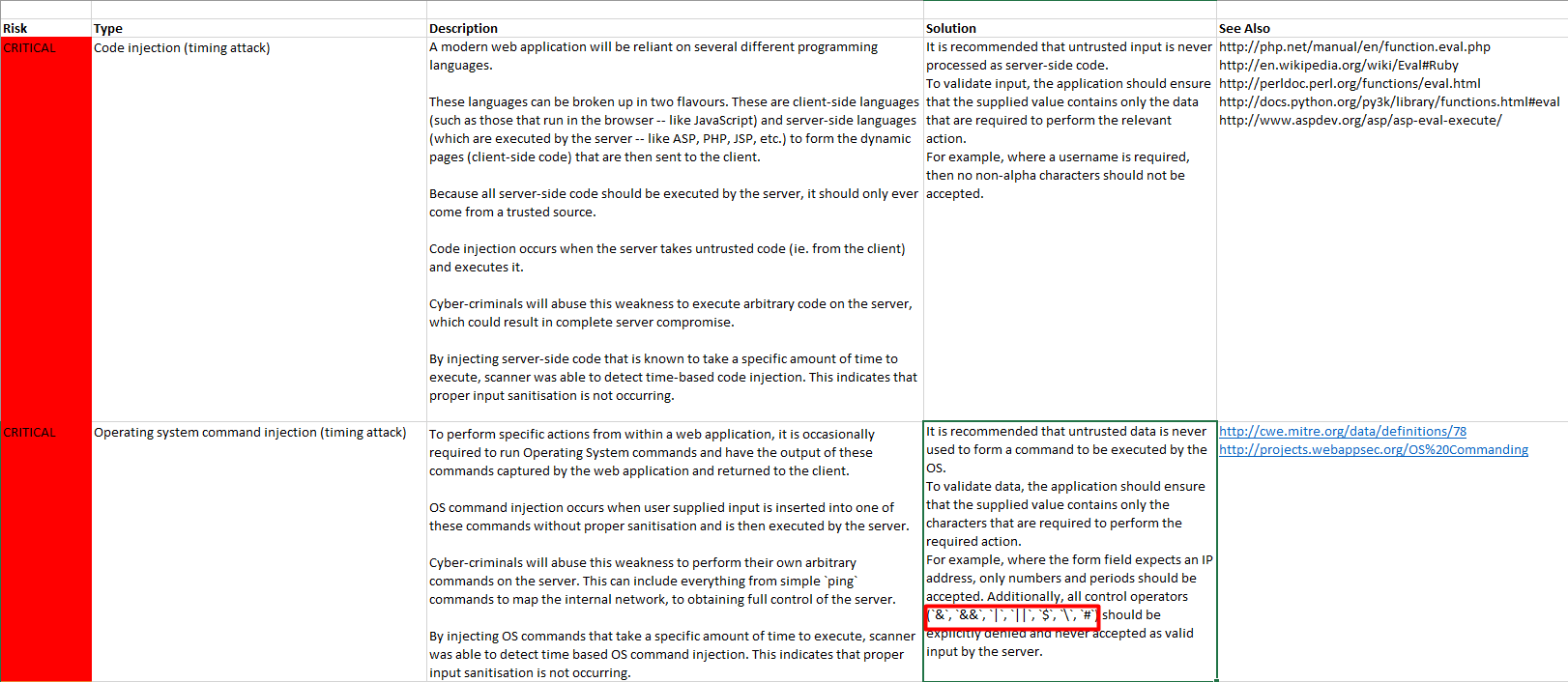
the problem is that the scan shows vulnerabilities of comman injection, system operative injection and sql innjectios, seeing the results I see that they are due to special characters that are being added in the request payload and which shyni is not blocking to avoid injections,
evidence
The question is, is there a way that the prefix of the payload that is the one that contains the special characters that general the alert of the scan can be removed without damaging the functionality? Or is this something that cannot be configured and is it typical of R and Shiny?