Hi,
up to now we have been using our Posit Connect with LDAP/AD Authentication and have been hosting Plumber APIs as interfaces to our models for other applications in our organization.
As per the latest changes, it is not possible anymore for Anonymous users (or Applications in our case) to use interactive content, such as Plumber APIs.
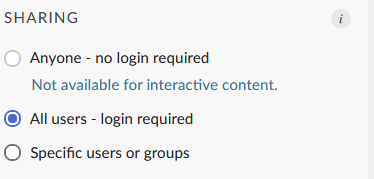
Hence, we changed to OAuth2 Authentication, following the migration guide and everything. On the user level everything works as intended.
Our understanding was, that we can now let Applications use our Plumber APIs via JWT token.
We generated a token and created a user on the Connect server by API with the email identity just like on our OAuth2 instance with the same UUID.
Afterwards we try to call our Plumber API like this:
library(httr)
myurl = "https://ourConnect/PlumberEndPoint"
accessToken = 'myJWT'
bdy = read_lines("myTst.json")
headers = add_headers(Authorization = paste0("Bearer ", accessToken))
res = POST(url= myurl, config = headers, body = bdy, encode = "raw")
We end up with this error message:
res$status_code
[1] 401
res$content
{"code":30,"error":"We couldn't log you in with the provided credentials. Please ask your administrator for assistance.","payload":null}
Does someone have a solution to this particular problem or does somebody know how we can make our Connect hosted Plumber APIs available to different Applications throughout our company?